The holiday season is exciting for retailers, bringing a surge in customers and sales. However, with this increase comes a heightened risk of cyberattacks. Hackers know that businesses are busy and distracted during this time, making it the ideal moment to strike.
Blog
Fortify your Android device and data with these new theft protection features
Safeguard your data with Android’s new features for combating theft
Say goodbye to sluggishness: Easy tricks to boost your iPhone’s performance
For many workers, iPhones are practical business tools — they make handling emails, presentations, and everything in between simple and easy. But these devices can become slow and unresponsive, which can disrupt your day and hinder productivity. By implementing the following five hacks, you can keep your phone running at its best and minimize sluggish performance.
VoIP optimization tips for Microsoft Teams
How to resolve Windows issues with an in-place upgrade install
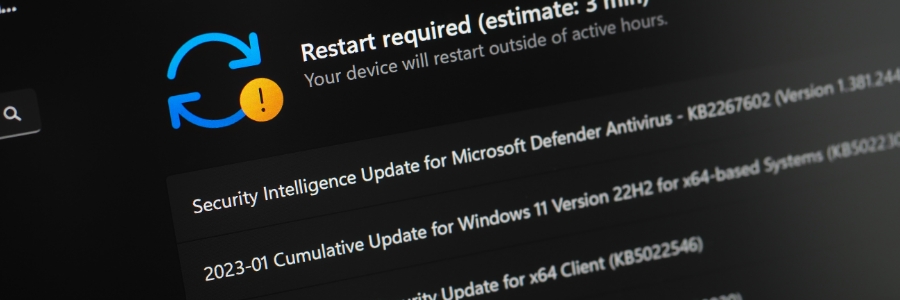
Is your Windows computer acting sluggish, displaying strange errors, or refusing to cooperate? Before resorting to a full reinstall, try installing a Windows in-place upgrade. This simple process can fix many common issues without wiping your data.
What is a Windows in-place upgrade install?
A Windows in-place upgrade refreshes your operating system without deleting your personal files, settings, or installed applications.
The power of Infrastructure as Code in scaling Internet of Things networks

The Internet of Things (IoT) has been key toward revolutionizing industries, connecting devices, and enabling data-driven insights. However, scaling IoT networks is becoming a challenge as the number of devices continues to increase. To address this, infrastructure-as-code (IaC) provides seamless scalability and efficient management of IoT infrastructure.
How identity and access management enhances zero trust in healthcare security

Many healthcare organizations are adopting zero trust security models to boost the protection of patient information from growing cyberthreats. To enhance the effectiveness of a zero trust model approach to security, it's crucial to integrate identity and access management (IAM) into security measures.





